Table of Contents
Protecting against outgoing SPAM
There are two good reasons to attack webservers :
- to install phishing web sites
- to use these web servers to distribute spams redirecting users to the phishing web sites.
So, webservers running vulnerable applications are the paradise for this kind of activity. But sometimes, some webmail accounts may be broken if the password is weak. Once the intruder gets into an account or succeeds to install some kit, he's able to send tens of thousand messages an hour…
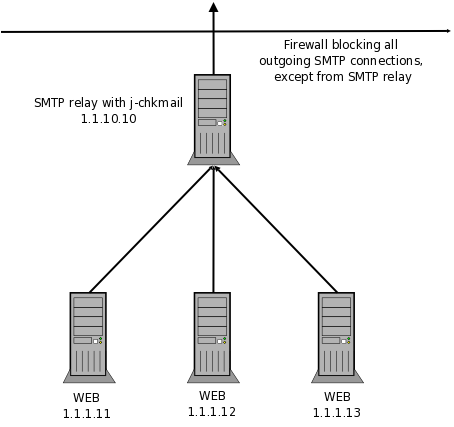
One easy solution to this problem is to close, at the firewall, all outgoing SMTP connections, except for the official mailserver and for the “relay”. The idea is to force all outgoing connections to pass through this relay. And at this relay, you'll surely install ze-filter and configure it to relay messages from webservers at some limited rate.
If the webserver gets compromised, it will send some spams, but at a really low rate, much slower than intended by spammers. Some spam will get out of your domain, but you'll be able to monitor, detect unusual activity and act.
Webservers configuration
Web applications shall be configured to allways use local sendmail or command line mail command to send messages. Either way, web applications shall never use direct SMTP connections to send messages, as output SMTP connections are blocked by the router.
At the webserver, create a sendmail mailertable with the content :
. esmtp:[1.1.10.10]
If you use postfix, it seems to me that the mailertable is defined at some file named “transport” or similar.
As a suggestion, sendmail shall be configured to run the queue each 5 minutes, with messages older than 15 minutes (not newer than 10 minutes).
That means, sendmail shall be launched as :
# /usr/sbin/sendmail -bd -q5m
and sendmail configuration shall contain :
O MinQueueAge=15m
The SMTP Relay
At sendmail access database (at 'relay'), configure :
Connect:1.1.1.11 RELAY Connect:1.1.1.12 RELAY Connect:1.1.1.13 RELAY
At ze-policy.txt (at 'relay'), you can put (don't forget to enable these checks) :
CHECK_CONN_RATE YES CHECK_OPEN_CONNECTIONS YES CHECK_NB_RCPT YES CHECK_MSG_RATE YES CHECK_NB_MSGS YES
ConnRate:1.1.1.11 50 ConnOpen:1.1.1.11 5 MaxRcpt:1.1.1.11 50 MsgRate:1.1.1.11 40 MaxMsgs:1.1.1.11 10
These limits may not be the best for your installation, and surely aren't.
To find the best values, you shall check, in normal conditions, both the mail queue of the web server and ze-filter logs (on the relay). A good operating point is when messages are delayed from time to time.
Also, keep in mind that the ideal operating point may not be the same for each of your web servers.